Conversations often touch on the topic of security.
But when you think about security, do you have a clear picture in mind? For most, security is purely about hardware cameras, alarm systems, beams, guards, or maybe even a couple of dogs on the property. Nearly 90% of all RFQs, tenders, and quotes for security focus solely on hardware. However, hardware is just one part of the equation. True security requires multiple elements working together to be effective and ensure that solutions function as they should. # Security Risk Assessment
We recently carried out an independent security risk assessment for a residential estate in Nelspruit, revealing risks that conventional assessments often overlook. This enables us to propose practical measures that improve the overall safety and security of the community.
If you would like to learn more about our assessments or have specific topics you would like us to cover, please email your suggestions to andre@alwinco.co.za. We will create and publish articles on our website based on your interests.
 You’re not wrong to think of these components.
You’re not wrong to think of these components.
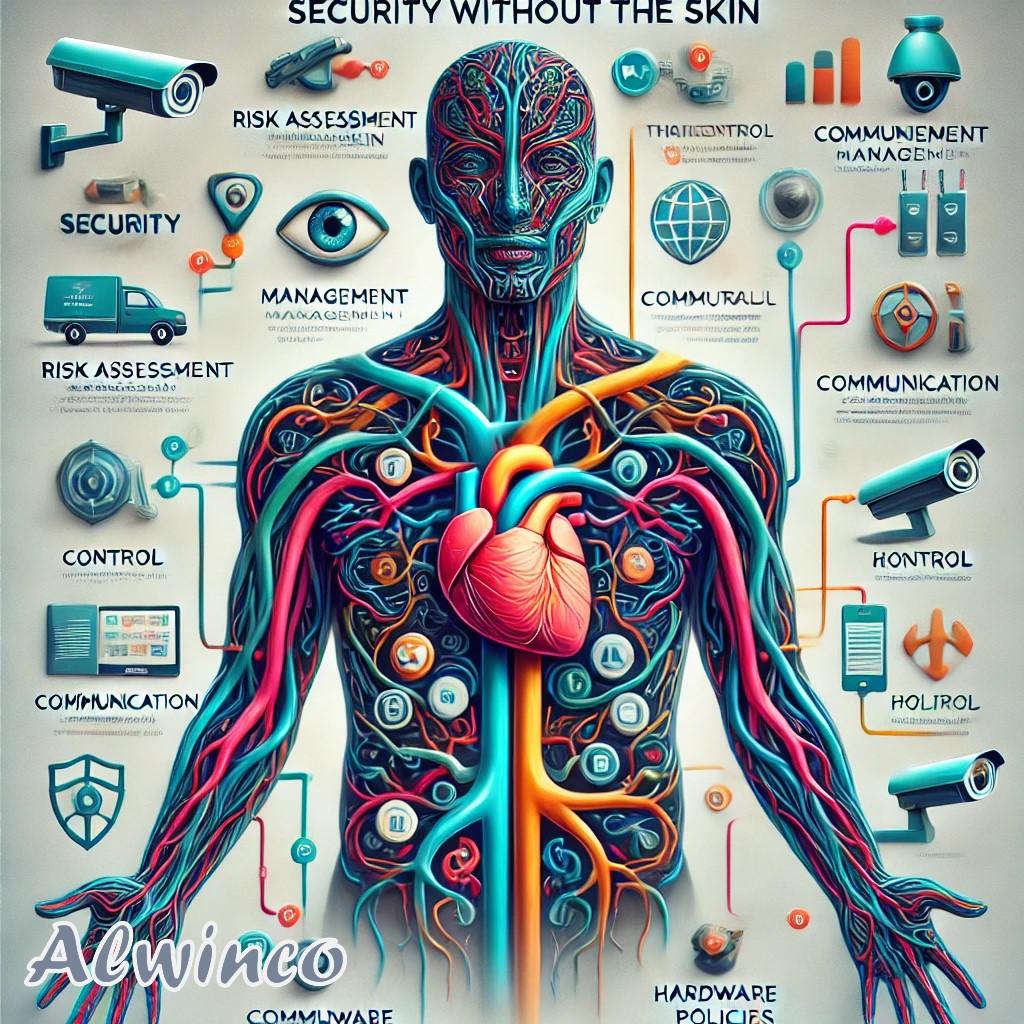
But that’s precisely what they are—just pieces of a much larger security picture. These components are merely building blocks, not the complete solution. When you think of a human being, you immediately picture arms, legs, a head, and a torso. But if you take a moment to consider it further, you’ll realize there’s much more to a person than just the physical body. Security works the same way. Now, imagine stripping away the skin of a human body. If you’ve never seen it before, I can assure you it’s not a pleasant sight. But doing so reveals everything hidden beneath the surface.
In Figure 1,
We’ve done the same with security we’ve pulled back its ‘skin.’ It may seem chaotic at first, but we used colors to distinguish the elements that make up the full picture. Laying the Foundation for Security
Security always begins with a security risk assessment.
This process is the first step before making any security-related decisions or investing in hardware or software. The security risk assessment identifies your security risks and provides the necessary guidance on how to mitigate them.
As shown in the illustration, the security risk assessment leads to risk-specific recommendations. From there, the process moves to RFQs and cost calculations. Only once the assessment is complete and the recommendations are approved does the sourcing of hardware take place. Remember, each section in this illustration interconnects to ensure optimal system functioning.
The lines connecting each section can be compared to the arteries in the human body; they represent the flow of data, connections, and critical information. One of the biggest mistakes people make with security is skipping the first and most crucial step: a security risk assessment.
Looking at crime statistics, it’s clear that most security structures are built on guesswork.
Decisions are made without facts, research, or a proper understanding of the risks involved. The second biggest mistake people make is overlooking the security network. A security network consists of interconnected cables or electronic devices that allow security data to flow seamlessly from one point to another. While wireless connections are now commonly used instead of physical cables, the network remains a critical component.
There are two types of security networks.
One is represented in the illustration, showing the broader structure, while the other exists within sections such as control, management, and security profiles, where everything is interconnected and works together to ensure the system functions as intended. In the illustration, you’ll notice that management is at the center, connecting to every aspect of the security structure. Management consists of various components, including control, hardware, the security plan, communication, processes, and policies. Without communication, control cannot exist. Similarly, management, communication, policies, and procedures are all interconnected, reinforcing one another. The security plan is directly tied to the security risk assessment, as the solutions are based on identifying and addressing the specific security risks.
A Best-Guess Approach
If you look at the illustration and remove the security risk assessment (which is precisely what happens in most security structures), you’ll see that there’s no research, no factual foundation, and no clear direction for solutions. As a result, security decisions are based on assumptions rather than facts. The security risk assessment, along with its recommendations, serves as the research needed to determine which solutions will effectively eliminate risks. This is where everything begins. It provides the framework for understanding security, guiding the approach, and ensuring that the right hardware is implemented to remove opportunities for crime.
When control is removed from the security equation, it quickly becomes clear that everything else begins to unravel, leaving various loose ends.
Most security companies and structures lack standard operating procedures (SOPs). For over 30 years, the same copy-and-paste method has been used for SOPs. The unfortunate reality is that many people aren’t even aware of the differences between the three types of SOPs that are in use today. Without an SOP, there is no security plan, nor any real control or communication. Removing the policies and procedures only makes matters worse, causing the entire system to break down. Policies guide the hardware, which in turn connects to control, communication, and management.
In the numerous security risk assessments we’ve conducted, we’ve found several of these essential components missing.
The result was always clear in the security structure’s performance. When even a single element of the security framework is absent, the entire security system is bound to fail.
There’s a reason we say a golden thread runs through the entire security structure. Every component is interconnected; one section cannot function without the one before it. Removing a single section will impact the entire system. It’s like an intricately woven tapestry; cutting even a single thread will eventually cause the whole thing to unravel.
As mentioned earlier, each section in the illustration has multiple facets that must work together for the system to function properly.
Take the various types of hardware: cameras, property lines, access control measures, alarm systems, and everything in between. All of these elements must not only work individually but also communicate seamlessly with one another. Moreover, when all the hardware communicates, the information has to be directed somewhere; that’s where control comes in.
 Command and Control
Command and Control
Some establishments refer to this area as the control room. The control function ensures that information is filtered and directed to the right people who can take appropriate action when needed. This is all part of the policies, procedures, and, ultimately, the security plan. Remember, only by implementing SOPs can you achieve control. Control and management, closely tied to communication, instructions, policies, and overall management, drive this structure.
Can you see the connections? Can you understand that you can’t simply remove a section and expect the system to continue functioning? Despite this, it seems we continue to do the impossible here in South Africa: removing multiple sections and still expecting security to work. As the crime statistics of our beautiful country clearly show, this approach simply doesn’t work.
When we conduct a security risk assessment, we always hope to find all the necessary sections in place.
Unfortunately, this is rarely the case. So, what does it truly mean to be in control of your security? I could explain it in detail, but that would require a 300-page document. In simple terms, being in control means having real-time awareness of what is happening at any given moment, with the ability to take swift and informed action when required. This level of control ensures that security systems are not only reactive but also proactive, allowing for immediate responses to threats and minimizing vulnerabilities. It’s about having the visibility and capability to make decisions that align with the overall security strategy, ensuring both the prevention of incidents and the rapid mitigation of any risks that arise.
What does communication really mean?
Communication isn’t just a single email or phone call; it goes far beyond that. Every element of security must be capable of communication, whether it’s between hardware and software, hardware and a person, or even between individuals. Without communication, there are no policies or procedures, and ultimately, no security plan. It’s the foundation that ensures everything operates cohesively and efficiently.
If you want to assess whether your security is up to standard,
Look at the illustration, follow it step by step, and identify the components present within your security structure. This will give you a clear indication of where your security measures stand. Additionally, elements such as the master copy, control registers, and maintenance are all integral to control and management. While these haven’t been included in the illustration, it’s crucial that they are part of your overall structure. There are about 12 essential control registers that should be in place, though they often aren’t. Training also plays a vital role, forming a key part of management, control, and procedures.
Seeing the Heart of Security
If you look closely, you’ll notice a heart included in our diagram. It’s not there just for decoration, and its placement is intentional. The heart symbolizes the control room, or the information center. The center is where everything converges. Whether you’re managing a large corporation, a small business, or even a home, it still needs a heart. An information center is necessary to filter all data and information into the appropriate channels.
CCTV cameras act as the eyes, while PTZ cameras serve as the neck of the ‘security body.’
Many companies attempt to run their security structures without a heart, and this approach never works. Just as a human body cannot function without a heart, security structures cannot function without control or a control room. Every element of security flows through the heart, which is why it’s the most important component.
Just like the human body, security also requires a brain to operate effectively.
Here is where artificial intelligence (AI) comes in. However, AI requires control and understanding, just like everything else. Uncontrolled AI can complicate security, and we’ll explain this in greater detail in a future article. To give you an idea of the vast network within a security structure, the illustration represents only a fraction of the information, much like a needlepoint on an A0-sized piece of paper. The rest of the paper still needs to be filled in.
Security managers play a vital role at the core of any security system, whether for a small property, business, or large corporation.
They are responsible for maintaining balance and ensuring the security structure operates effectively.
Click here to read more on Alwinco’s security risk assessment methodology.
Please note: “Property” refers to homes, businesses, campuses, hospitals, estates, farms, schools, government-owned entities, and government properties.
By Andre Mundell, Alwinco. # Security Risk Assessment Cape Province
Furthermore, in addition to other major cities in Gauteng, our services for assessing security risks are accessible in Arcadia, Bloemfontein, Bluff, Johannesburg, Erand Gardens, and Midrand.